View, analyze and report on mobile evidence involved in an investigation OpenText™ EnCase™ Mobile Investigator…

MD-NEXT
Mobile forensics software for smartphone, feature phone, drone, smart TV, wearable, IoT device, USIM card, SD memory card, JTAG board and chip-off memory
MD-NEXT is a forensic software for data extraction from diverse mobile and digital devices. It supports physical and logical extraction methods for Android, iOS, Windows OS, Tizen OS, and other mobile OS.
MD-NEXT supports data extraction from MD-READER(Chip-off memory), MD-BOX(JTAG board), USIM reader, SD memory reader, OS backup protocol, agent app, and new cutting-edge extraction methods
Key Features
Complete Mobile Data Acquisition Tool
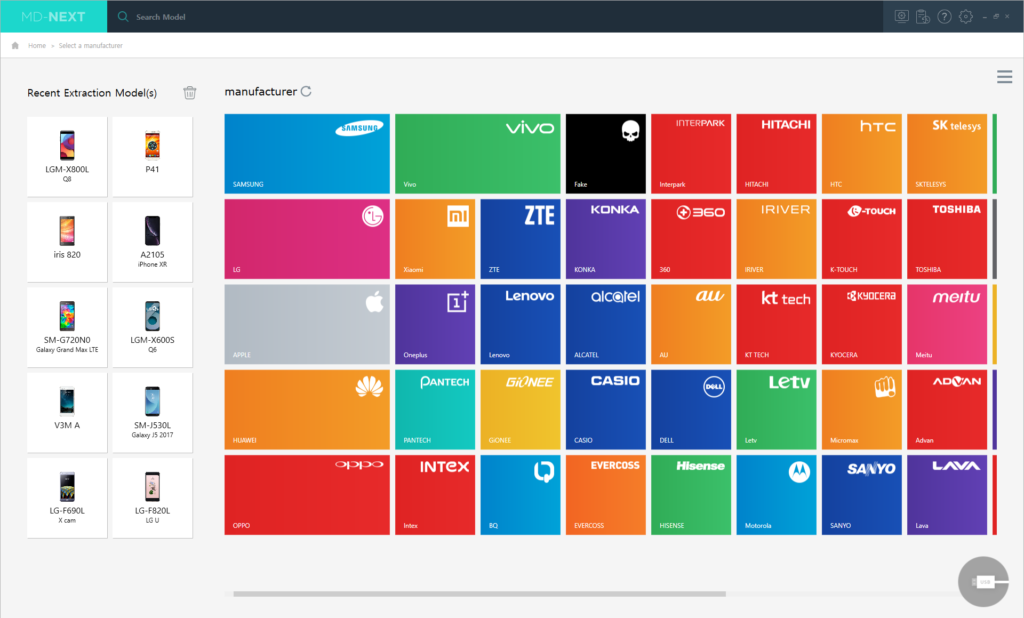
- Supports data acquisition for various global smartphone manufacturers (Samsung/Apple/LG/HTC/ZTE etc.) models
- Supports China Manufacturer (Huwei/Xiaomi/Oppo/Vivo, etc.) for large quantities of models
- Supports extraction of IoT device, AI Speaker, Smart TV and Drone
Advanced physical extraction features
- Supports Bootloader, Fastboot, MTK, QEDL, Custom Image Android Rooted, iOS Physical, DL, JTAG, Chip-off, SD Card, Removable Media
- ADB Pro extraction: Supports data acquisition using vulnerability attacks from Android-based devices
- JTAG pin map viewer and connection scanning with AP
- Drone data extraction – DJI (Phantom, Mavic), Parrot, PixHawk
- AI Speaker Chip-off extraction – Amazon Echo, Kakao Mini, Naver Clova
Supports diverse physical data reader hardware
- JTAG Reader (MD-BOX)
- Memory Chip Reader (MD-READER)
- SD Memory Reader and USIM Reader
Advanced logical extraction features
- Supports Android Live, MTP, iOS full filesystem Backup, Vendor backup protocol, Local backup, USIM
Supports extraction and decryption of the latest Asian phone
- Physical extraction through all lock bypass(KNOX, FRP/OEM, Screen Lock): Samsung Galaxy S/J/A/Note series
- Unlock screen: Samsung Galaxy S/J/A/Note series
- ADB Pro physical KNOX bypass – Samsung Galaxy S/J/A/Note series
- Vendor Backup protocol extraction – Samsung, LG, Huawei
- Local backup extraction – Huawei, Xiaomi, Oppo, Gionee
- Physical extraction for Japanese manufacturer model – Sharp, Sony
Supports the latest iPhone logical extraction
- iOS keychain extraction
- Logical extraction for iPhone up to XS/XR model
- The decryption of backed up data for the latest version of the iOS device
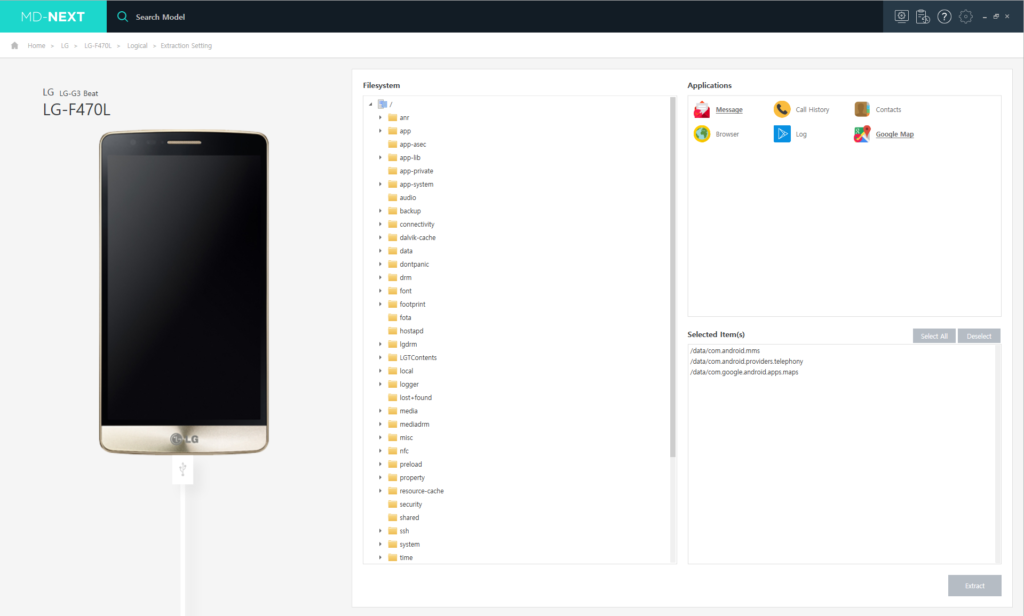
Selective extraction for privacy protection
- Supports selective acquisition of partition, file, category, and app
Special extraction features
- Supports user-defined extraction for unlisted models using pre-defined methods
- Supports Google cloud drive extraction
Useful extraction utilities
- Supports auto recognition and decryption of partition table and encrypted partition
- Supports automatic firmware restoration and retrial after restoration failure
- Supports resume of extraction
- Supports merge of multiple image file – MDF and binary file
- Support acquisition from PC backup files: iOS, Samsung, LG
Assurance of evidence data integrity
- Supports write-protection to every evidence data
- Supports various hash algorithms(MD5, SHA1/224/256/384/512, RIPEMD128/160/256/320)
Easy and simple user-friendly UI
- Intuitive graphical user guide for each extraction method
- List of recently selected models
Data preview and save
- Supports preview of the extraction data – Hex viewer
- Sound alarm and TTS alarm for extraction status change
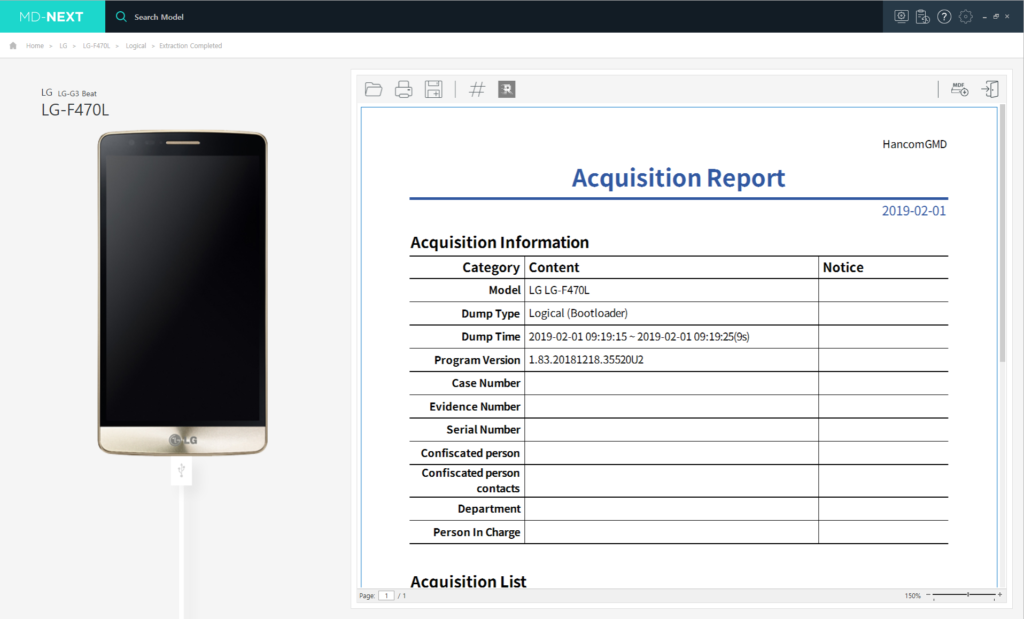
Reporting features
- Extraction information – Hash value, Time, Method and Filename
- Supports ‘Extracted File List’ generation with a hash value of each file
- Generate ‘Observation Confirmation Report’.