Digital forensic imaging for law enforcement and corporate investigations The increasing diversity, size and sophistication…

Belkasoft Evidence Center X
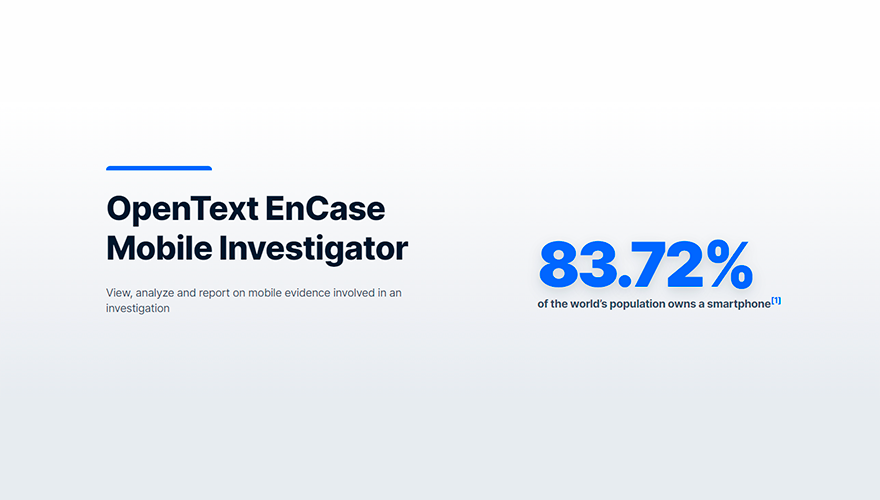
Belkasoft Evidence Center X is an all-in-one digital forensics and incident response solution for acquiring, locating, extracting, and analyzing digital evidence stored inside computers and mobile devices, RAM and cloud.
Product is offered in a number of editions.
BELKASOFT EVIDENCE CENTER X EDITIONS
X FORENSIC
X Forensic edition is the complete solution for conducting in-depth investigations on all types of digital media devices and data sources, including computers, mobile devices, and the cloud. Combining the functionality of X Computer and X Mobile editions with advanced features such as cloud data extraction, checkm8-based acquisition, and WDE decryption, it is an irreplaceable analytical tool for digital forensic laboratories of federal law enforcement agencies and state-level police departments.
KEY FEATURES
- All features of X Computer and X Mobile.
- Acquire and analyze data from cloud sources.
- Use forensically sound checkm8-based acquisition to extract data from the range of iPhone devices
(from iPhone 5s through iPhone X) and even from locked iPhones without a jailbreak. - Access devices encrypted with whole device encryption, such as APFS, Bitlocker, TrueCrypt and others.
X CORPORATE
X Corporate edition is the digital forensic and incident response solution with enhanced analytical functionality specifically developed to meet the business requirements of large corporate organizations, which prefer to have a DFIR team in-house or provide DFIR services. Corporate incident responders can take advantage of a combination of X Forensic capabilities and advanced X Corporate features—incorporated into the product specifically to respond to the demands of corporate customers.
KEY FEATURES
- All features of X Forensic.
- Investigate hacking and intrusions into Windows-based computers with the help of Incident Response module.
- Find intersections between the currently investigated case and other BEC X cases by using Cross-Case Search functionality.
X COMPUTER
X Computer edition is a cost-effective solution developed specifically for investigators in local police
departments, experts in small to medium consulting companies providing digital forensic and incident
response services, and individual customers such as private investigators or digital forensic consultants.
Customers who typically deal with only a few computer-related cases per year and/or have a limited
budget will enjoy the very affordable price of X Computer edition.
KEY FEATURES
- Extract data from hard drives, mount and analyze hard drives, disk images, virtual machines, and RAM.
- Mount third-party tools images (EnCase, FTK, X-Ways, etc.), L01/Lx01, DD images, archive files (such as.tar, .zip and others).
- Examine and analyze hundreds of artifacts: chats, browsers, mailboxes, documents, pictures and videos, system files.
- Use analytical features, such as Connection Graph, Timeline, advanced picture analysis.
- Perform in-depth examinations into the contents of files and folders on the device with File System Explorer. Find even more evidence with Registry and SQLite Viewers.
- Powerful file and data Carving feature helps to locate evidence that was deleted or hidden.
X MOBILE
X Mobile edition is a cost-effective solution developed specifically for investigators in local police
departments, experts in small to medium consulting companies who provide digital forensic and incident
response services, as well as individual customers (i.e. private investigators or digital forensic consultants).
Customers who typically deal with just few cases per year involving unlocked mobile devices, and usually
have limited budgets will enjoy the affordable price of X Mobile edition.
KEY FEATURES
- Acquire images of iOS and Android devices using standard backup as well as jailbreak-related methods,
lockdown files, MTP/PTP, MTK. - Extract full file system copy and keychain from iOS devices with the help of Belkasoft agent without
doing a jailbreak. - Mount mobile backups and third-party tool smartphone images (UFED, OFB, GrayKey and Elcomsoft
iOS images), chip-off dumps, TWRP images, JTAG dumps, etc. - Examine and analyze mobile artifacts—calls and messages, mailboxes, messenger apps data
(WhatsApp, Signal, Telegram, Snapchat, WeChat, etc.), social media apps (Facebook, Twitter, Tinder,
etc.), browsers, cryptocurrencies, and many more. - Use analytical features, such as Connection Graph, Timeline, advanced picture analysis.
- Perform in-depth examinations into the contents of files and folders on a device with File System Explorer. Find even more evidence with PList and SQLite Viewers.